DDoS
DDoS
Introduction
Denial-of-service (DoS) attacks try to make a service or network resource unavailable to its intended/legitimate users. Typically achieved by exhausting available resources by sending an excessive amount of traffic/packets/requests.
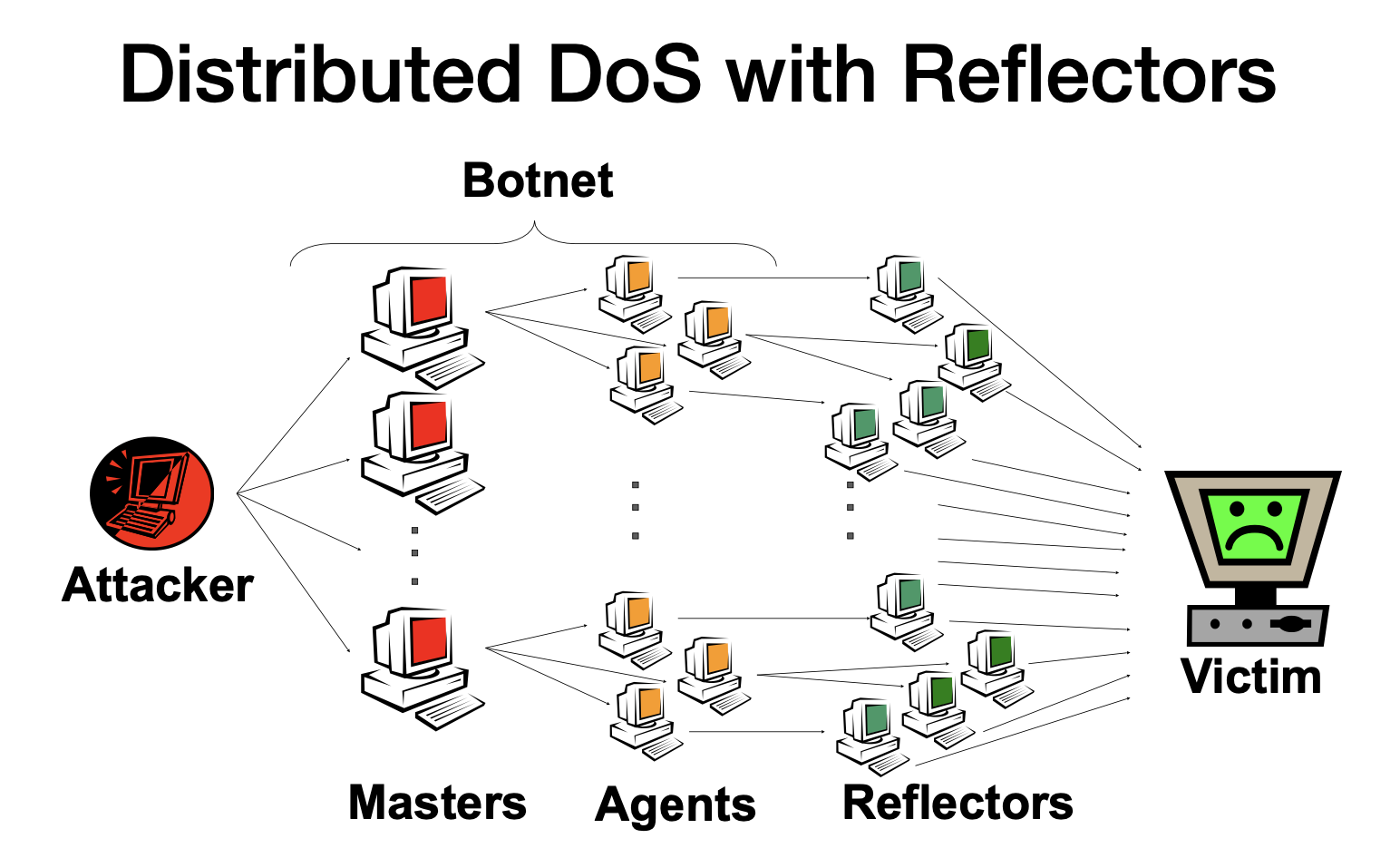
Distributed DoS (DDoS) attacks use many different sources simultaneously, often by creating and using botnets.
DDoS attacks are often used to extort companies: “Pay XX bitcoin and the attack will stop”
There are a few things that facilitate DoS attacks:
- Attacker controls significantly more resources than victim
- The server is openly accessible
- No authentication
- Attacker needs to expend significantly less resources than victim
- Attacker can hide its identity or continually change it
- Victim needs to expend a significant amount of resources before being able to assess the legitimacy of requests
- Attacker can instruct/trick other entities to send traffic on its behalf
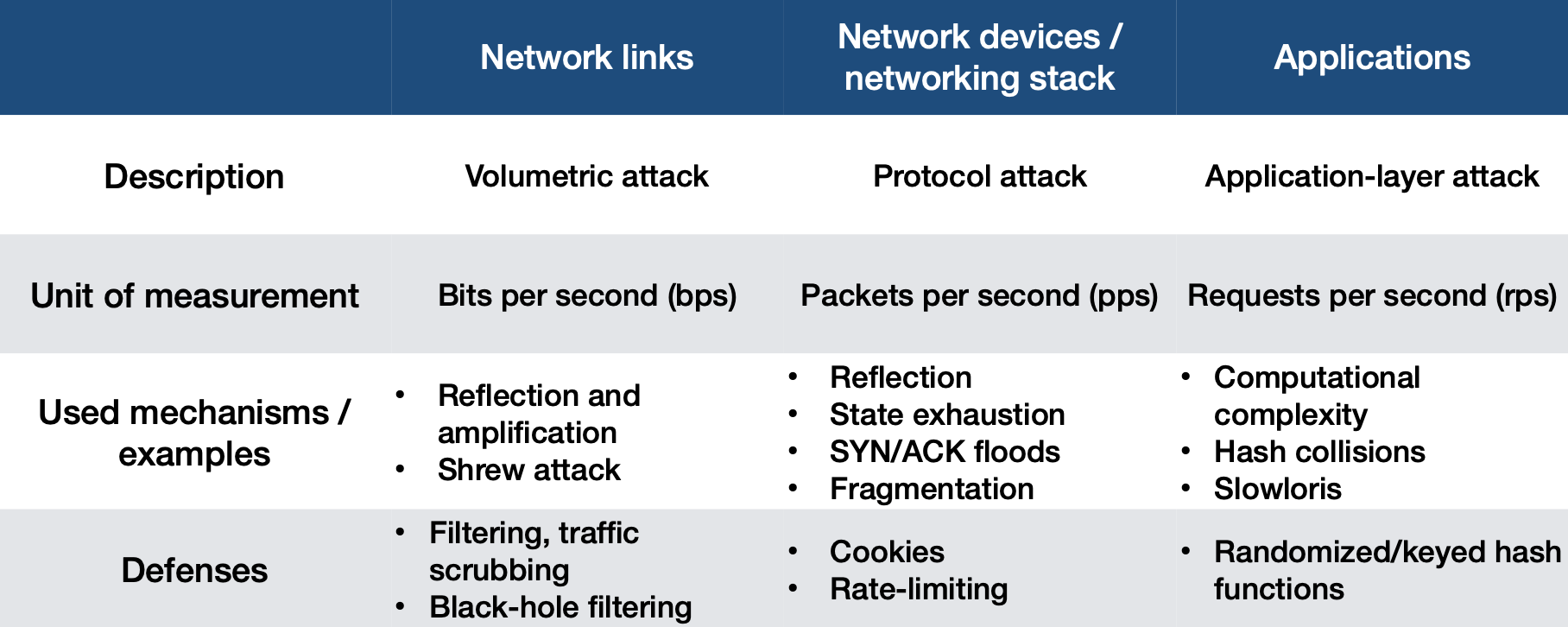
Main attack types
Volumetric attack
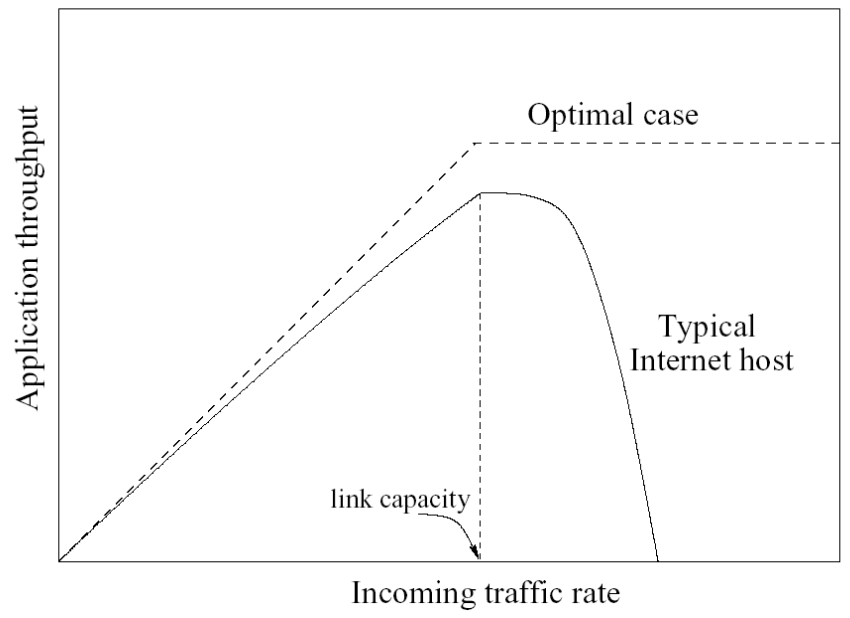
The goal is to consume the bandwidth either within the target network/ service, or between the target network/service and the rest of the Internet. These attacks are simply about causing congestion.
It’s measured in bits/s
Typical vectors:
- ICMP packet floods (including all ICMP message types)
- UDP packet floods
- Malformed ICMP, UDP, IP packet floods
- Reflection/Amplification — e.g.: DNS, NTP, memcache reflection
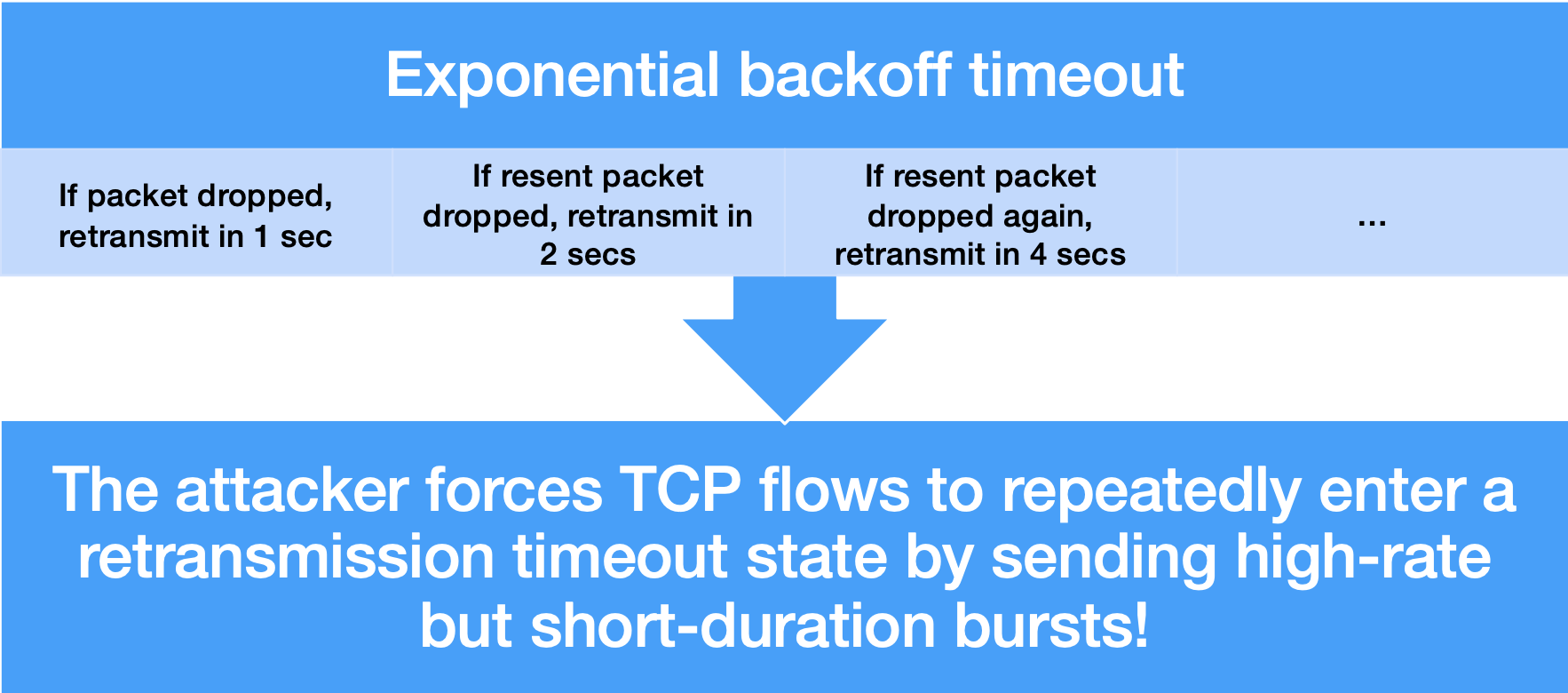
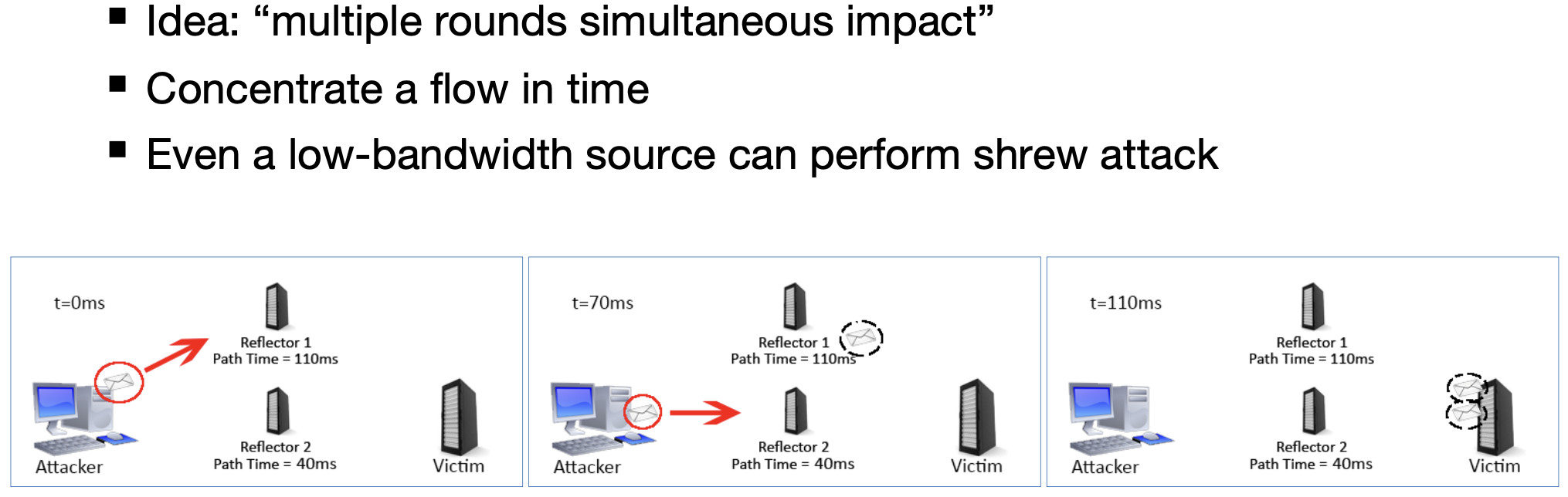
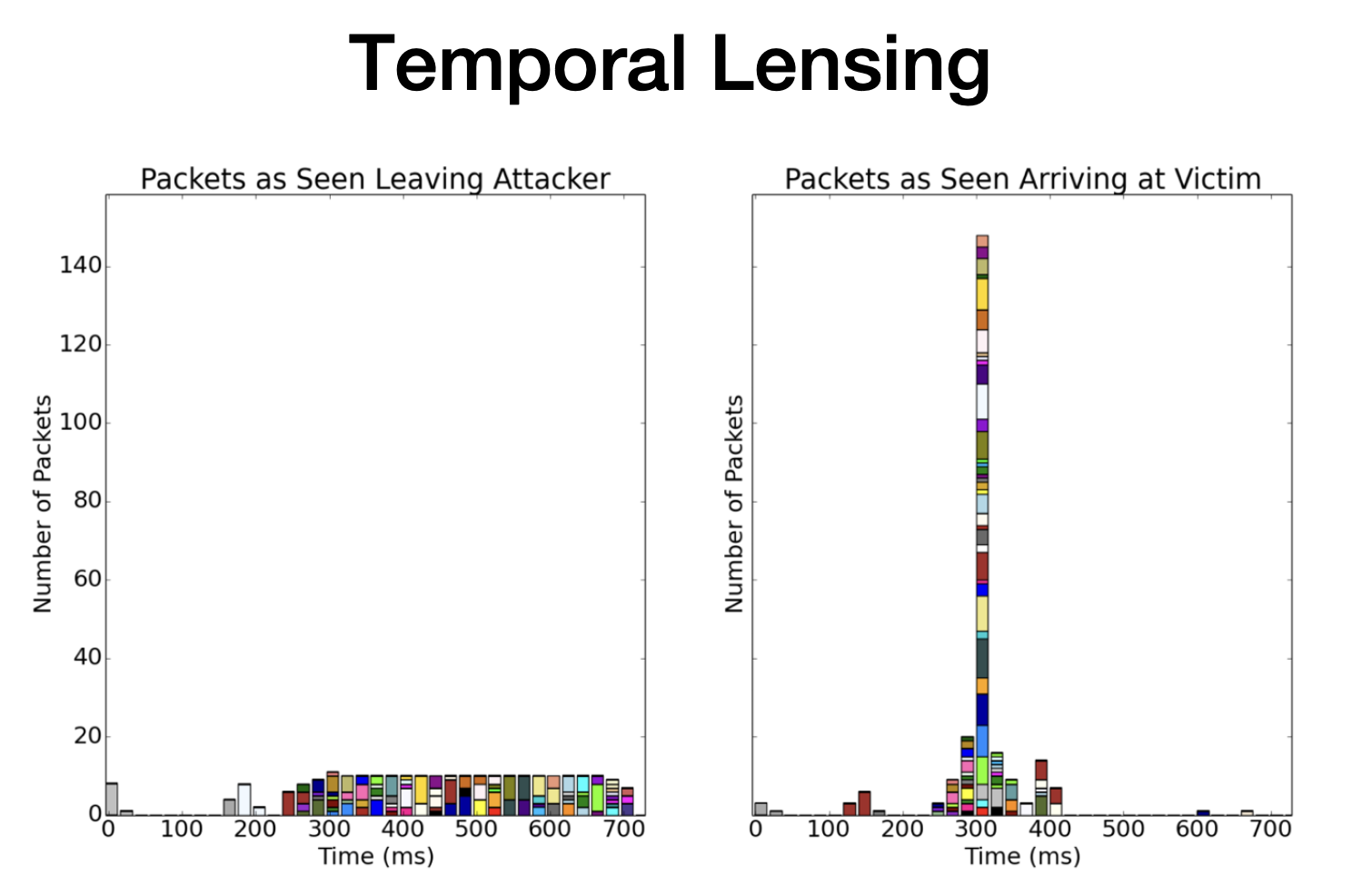
Shrew DoS Attack
Coremelt attack: Adversary controls many bots distributed across the Internet. Bots send traffic between each other, thus all traffic is desired by destination. Traffic is not sent to victim as in regular DDoS attacks. Adversary can exhaust bandwidth on victim link Result: attack traffic exhausts bandwidth in per-flow fair sharing systems
Crossfire attack: Adversary controls distributed bot army. Observation: due to route optimization, few links are actually used to connect a target region to rest of Internet. Adversary can contact selected servers to overload target links. Result: disconnect target region from remainder of Internet
Protocol attacks
It’s designed to exhaust resources available on the target or on a specific device between the target and the Internet. Devices can include routers, load balancers, or security devices.
Once the attack consumes a resource such as a device’s TCP state table, no new connections can be opened. Protocol DDoS attacks do not need to consume all of the target’s available bandwidth to make it inaccessible. They can take down even high-capacity devices capable of maintaining state for millions of connections
It’s measured in packets/s
Typical vectors:
- SYN/ACK floods
- RST attacks
- TCP connection floods
- Fragmentation attacks
- DNS, NTP reflection
NXDOMAIN Attack: the goal is to overwhelm victim’s authoritative name servers.
Idea: query many non-existent subdomains of victim domain. Resolver queries all authoritative name servers in turn Can use multiple DNS resolvers Can be sent from distributed botnet and via many different DNS resolvers Result: name server can no longer reply to legitimate requests
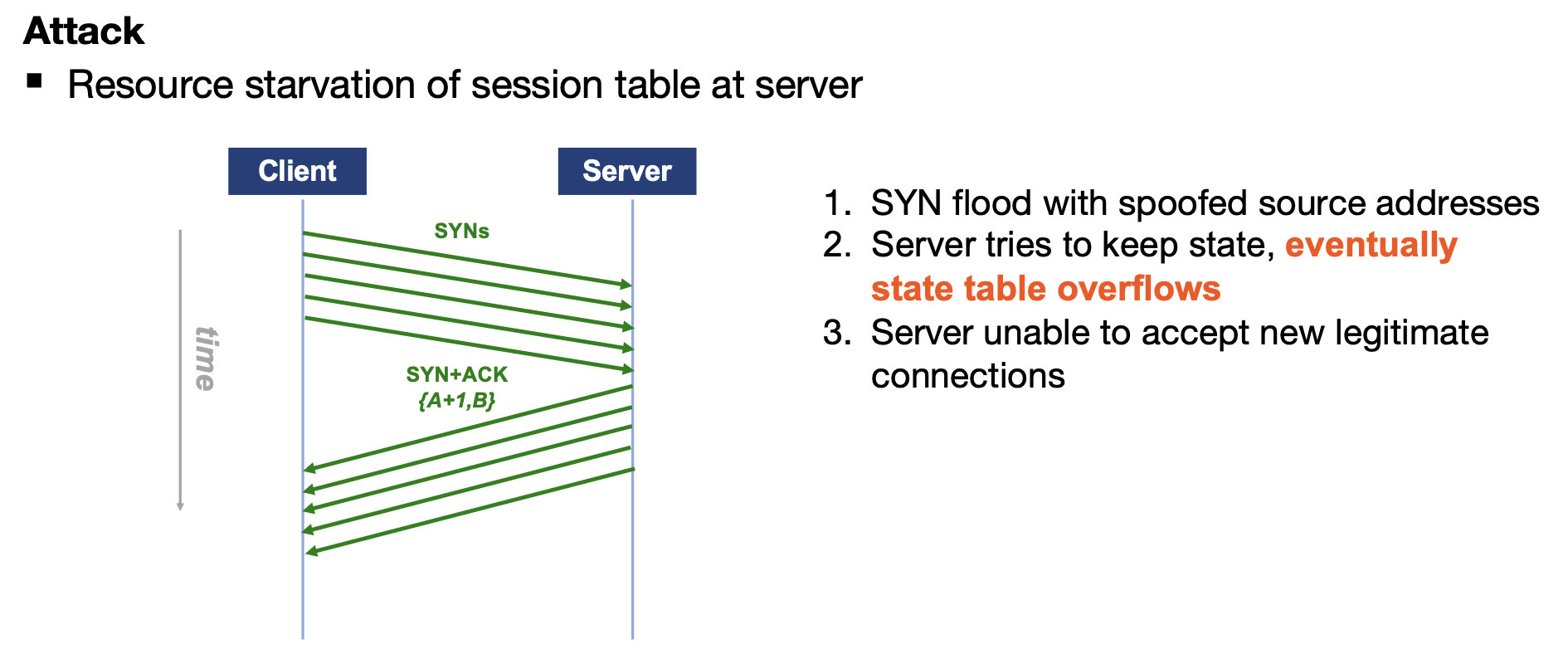
Session State Exhaustion Attack: exhausting the session state table of the server → Server can no longer accept new connections, existing connections are dropped, maybe the server / service crashes. This is mitigated by delegating the state-keeping to the client, by encoding the state in the reply.
SYN Flood Attack:
Application-Layer Attacks
It’s designated to target various aspects of an application or service at Layer 7.
Most sophisticated and stealthy attacks as they can be very effective with as few as one attacking machine generating traffic at a low rate. Attacks very difficult to proactively detect with traditional flow-based monitoring solutions.
Application-layer attacks are often referred to as stealthy or low-and-slow attacks
It’s measured in requests/s
Typical vectors:
- Layer 7 protocols, HTTP, SMTP, DNS, SNMP, FTP, SIP, etc.
- Application request floods
- Database connection pool exhaustion
- Reflection/Amplification
- Slowloris, slow post/read
- SIP invite flood
Algorithmic Complexity Attack: induce worst-case behaviour in a vulnerable algorithm. The larger the difference between the worst case and average case, the more vulnerable the algorithm.
Slowloris Attack: allows a single machine to take down another machine’s web server with minimal bandwidth Slowloris tries to keep many connections to the target web server open and hold them open as long as possible. It opens connections to the target web server and sends partial requests Periodically, it will send subsequent HTTP headers, adding to – but never completing – the request
Affected servers will keep these connections open, filling their maximum concurrent connection pool, eventually denying additional connection attempts from legitimate clients.
Mitigations: increasing the maximum number of clients the webserver will allow ! Limiting the number of connections from single IP address; require minimum transfer speed per connection; restrict the length of time a client is allowed to stay connected. Other mitigating techniques involve setting up reverse proxies, firewalls, load balancers or content switches.
Address Spoofing
Source address in IP header can be set by the sender. In a connectionless protocol (UDP), the server cannot verify the actual sender.
Possible defences against address spoofing:
- Address filtering by ISPs:
- Needs to be globally deployed
- Poor incentives for ISPs to deploy it (only customers of other ISPs profit)
- Use connection-based protocols (e.g., TCP)
- Additional latency
- Potentially additional DoS attack vector (state exhaustion)
- Cryptographic source authentication
- Additional DoS attack vector if built on (expensive) asymmetric cryptography
- Requires symmetric key distribution or PKIs
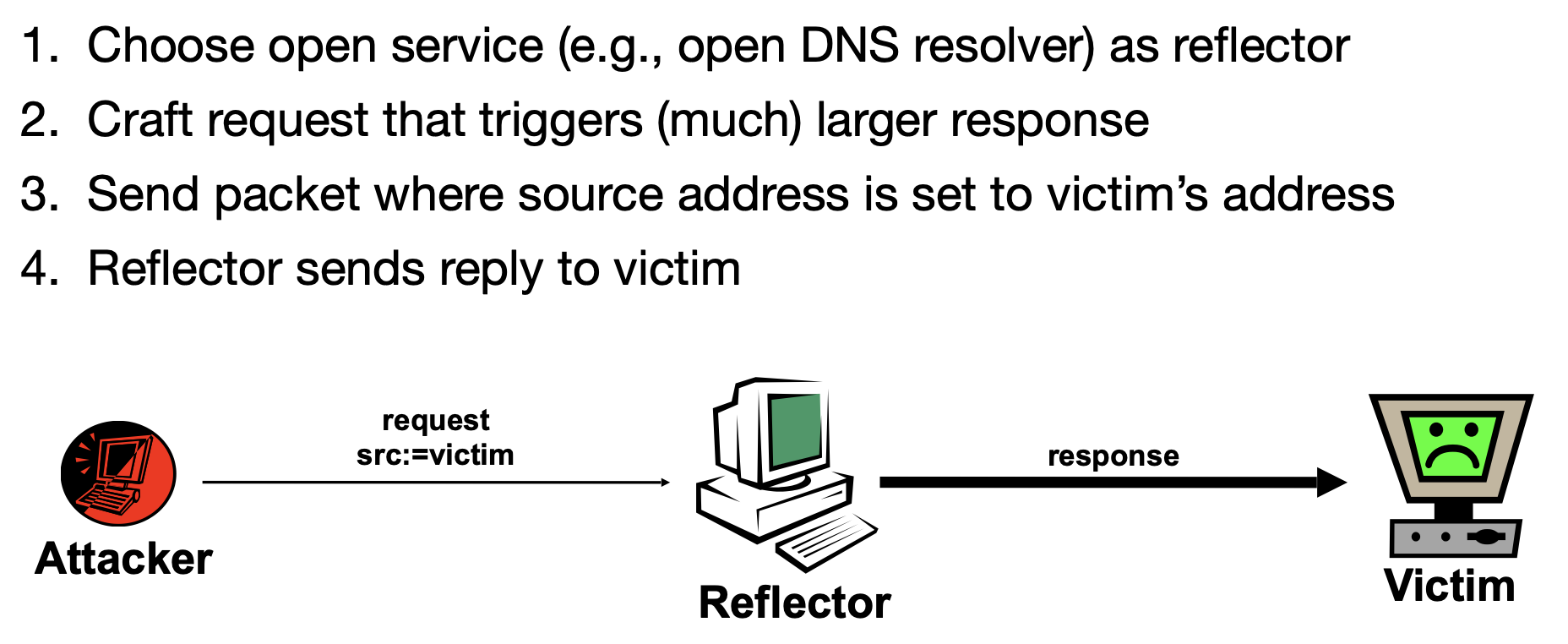
Reflection and amplification
Requirements:
- Ability to spoof source address
- Publicly accessible servers
- Ideally: response is (much) larger than request → amplification
- Either number of packets or size of packets increased