Network Security
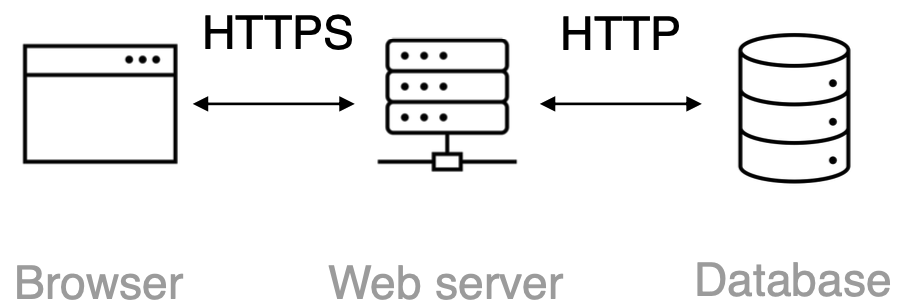
Now Network properties are successfully verified. But, are users reaching the correct website? Or… do they even reach the website? 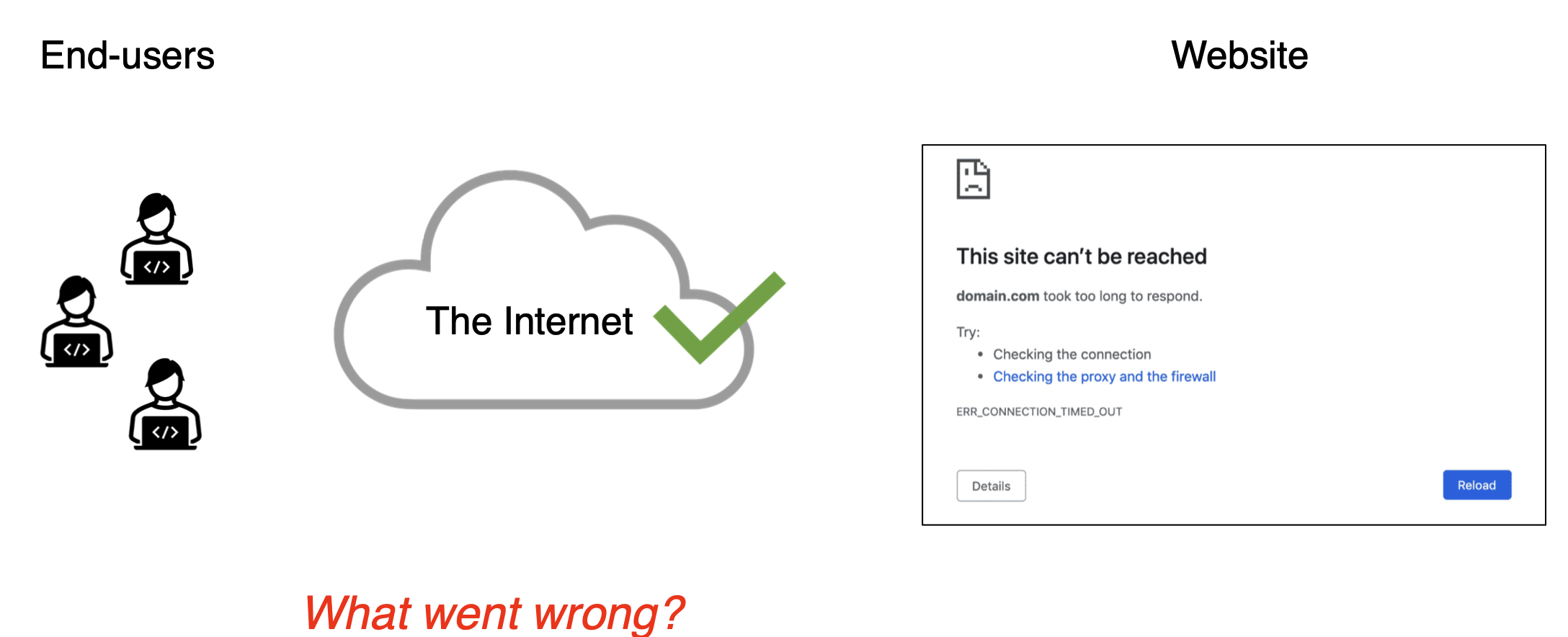
It’s likely due to a network attack that is causing failures! Network attacks are very common nowadays and they’re affecting many critical Internet services.
In this chapter, we will cover three important aspects in network security:
- Modelling network systems
- Finding network threats
- Addressing network threats
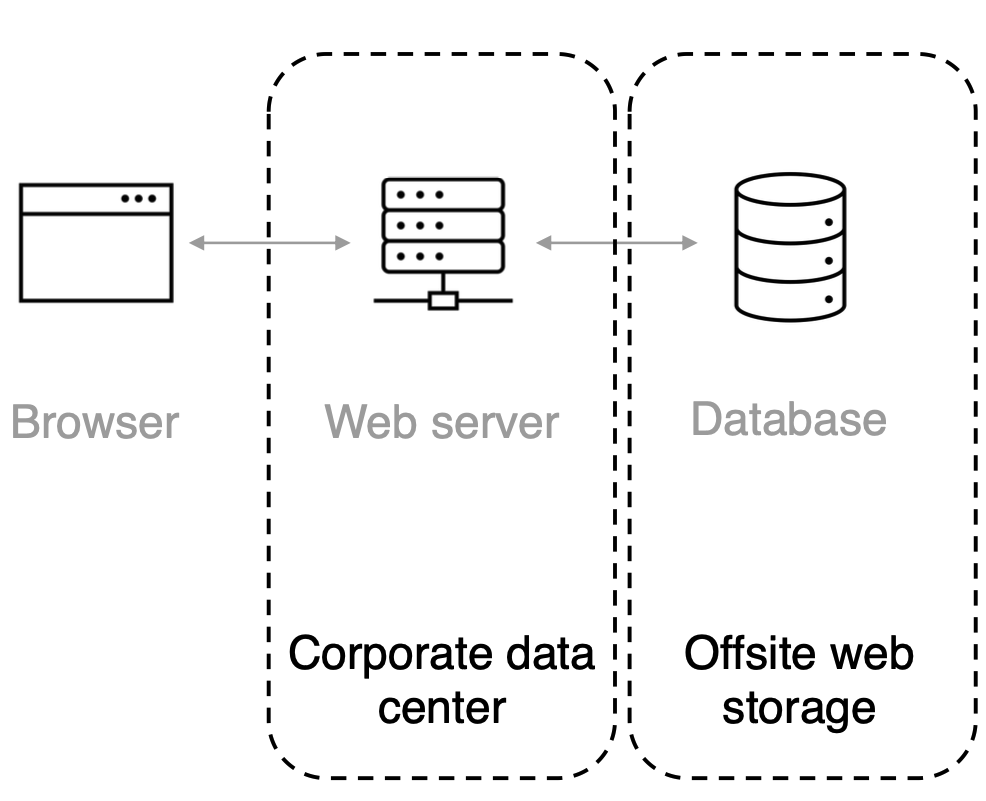
Modelling
We need to identify what the system consists of.
- What are the nodes? Identifying components of interest
- What are the connectivities? Indicate the protocols between nodes
- What are the trust boundaries? Define who controls what
Example
Tips
A few tips when modelling networked systems:
- Try to model all components
- Simplification is often needed for complex systems though
- Try to model the entire stack of protocols
- Threats may happen “cross-layer”
- Try to model different levels of trust boundaries
Finding threats
- STRIDE
- PASTA
- VAST
- SQUARE
We will try to find threats with the STRIDE methodology
STRIDE
- Spoofing
- Tampering
- Repudiation
- Information disclosure
- Denial of Service
- Elevation of Privilege
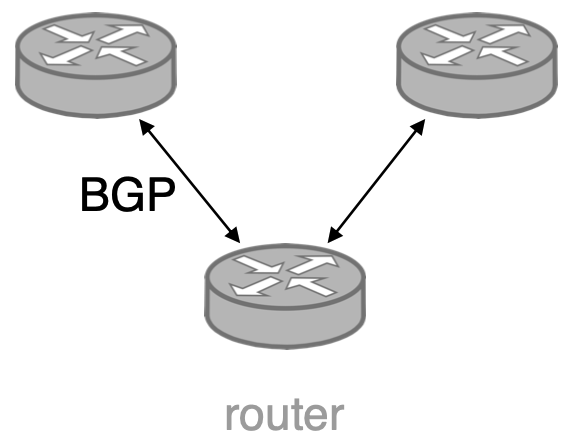
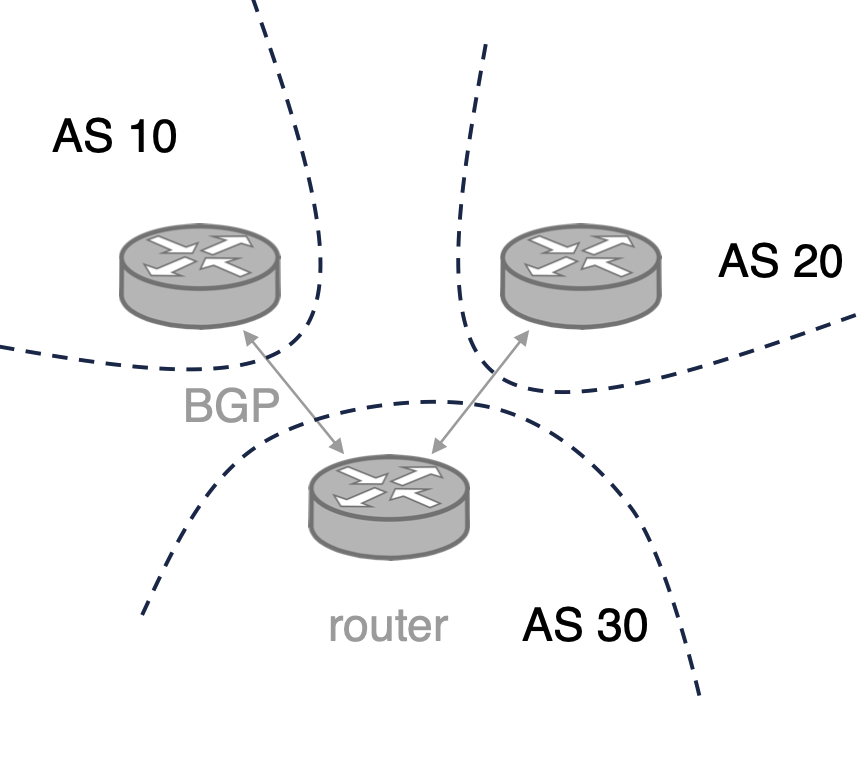
Let’s assume no threats within AS30 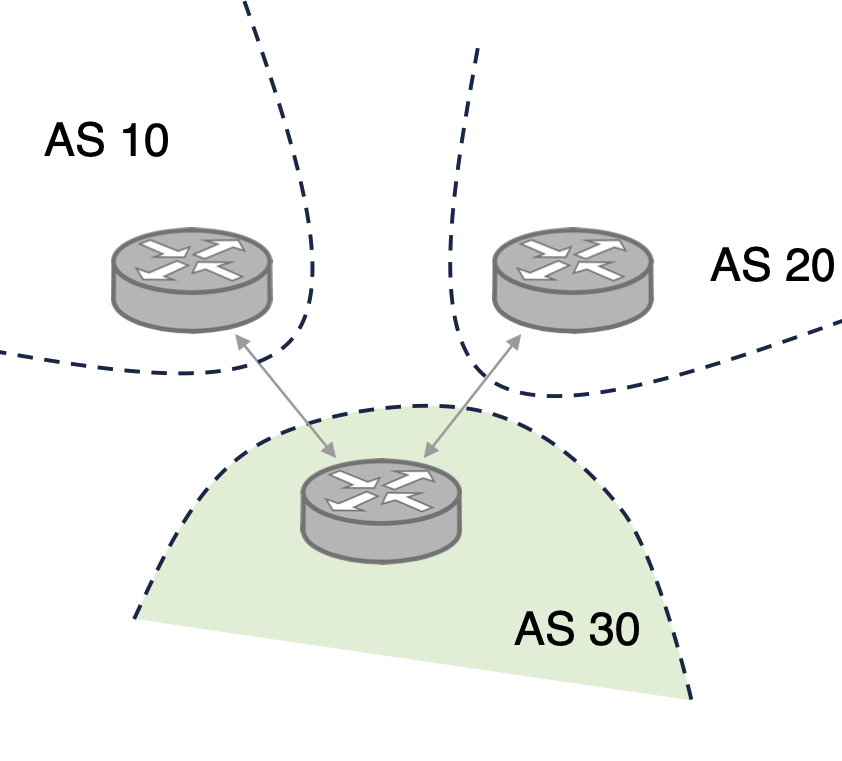
Spoofing threats
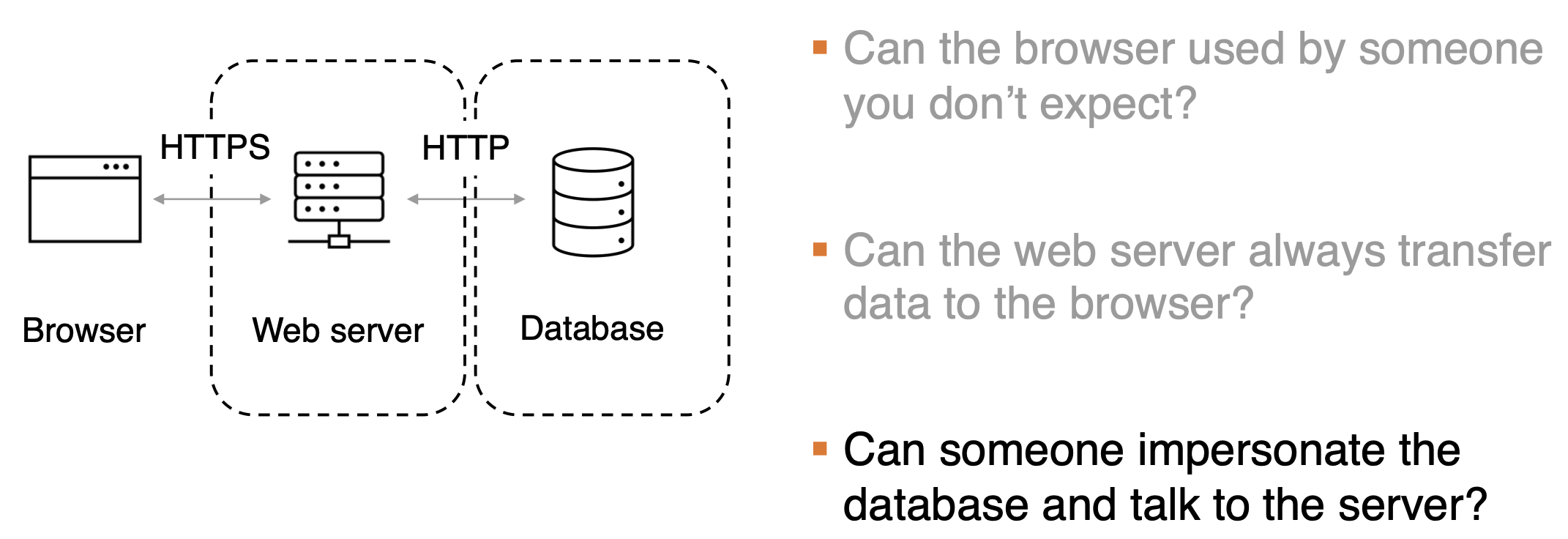
Can BGP messages sent to AS30 be spoofed with AS10’s router address?
Hint: BGP messages are sent over TCP!
YES! TCP sequence number attack!
May not be a concern nowadays though
Tampering threats
Can BGP messages sent to AS30 be added/modified/removed/replayed? 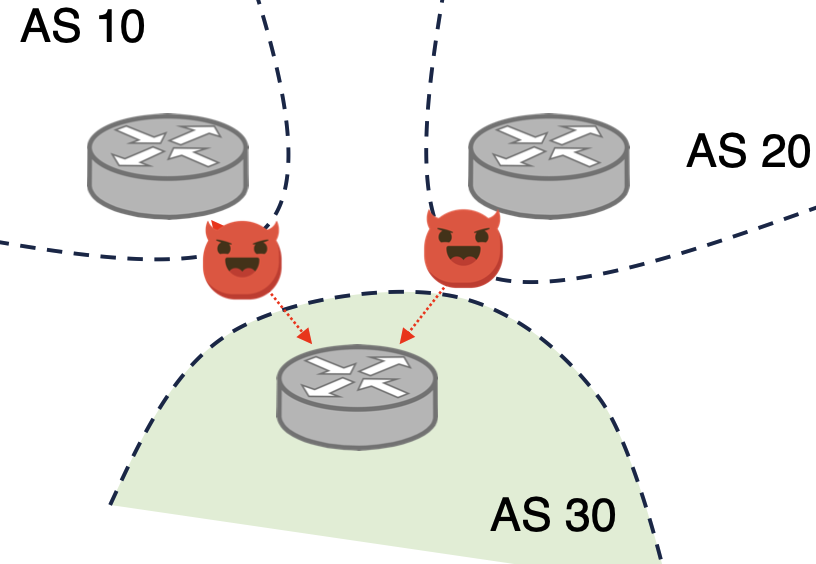
YES! By MitM attackers
Getting in the middle is difficult in practice
Repudiation threats
Claiming you were not responsible for something.
Can AS20 propagate a fake path (e.g., [10 20]) to AS30 and deny it?
YES! The path may actually exist! Repudiation usually appears in post-mortem.
Information disclosure threats
Exposing information to unauthorized people.
Can AS20 learn the business relationship between A10 and AS30? 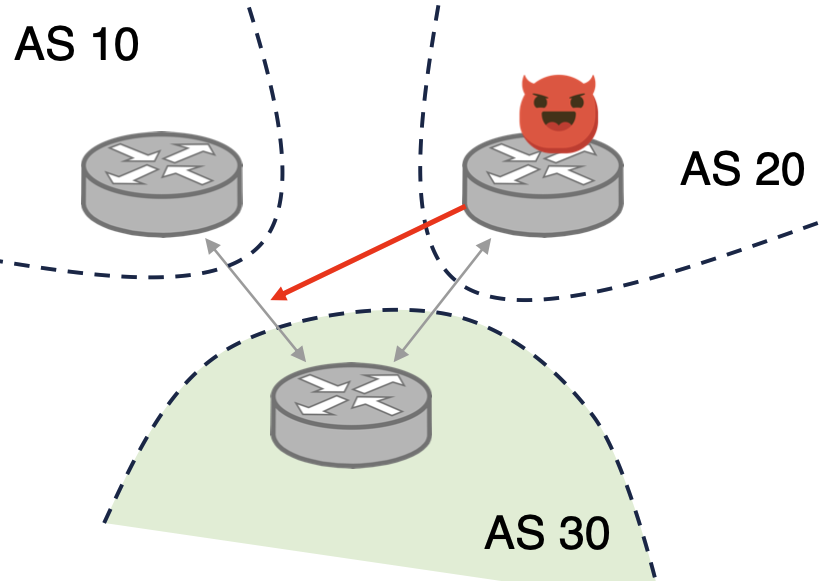 YES! But Relationship inference may be imperfect.
YES! But Relationship inference may be imperfect.
Denial of Service threats
Absorbing resources needed to provide service.
Can AS20 launch denial-of-service attacks against AS30’s router? 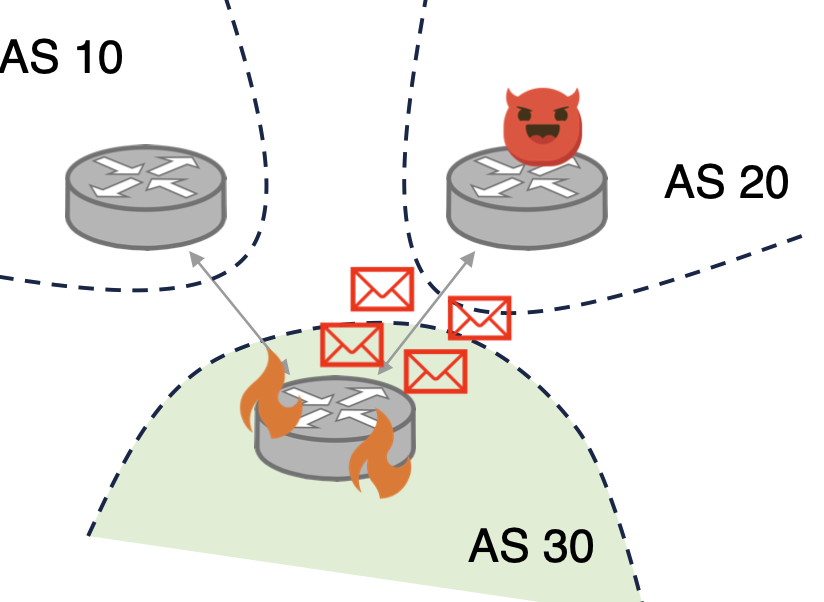
YES! By flooding BGP messages! Or in many other ways.
Elevation of Privilege threats
Allowing someone to do something without authorization.
Can AS20 advertise prefixes belong to AS10?
YES! Prefix ownership is not verified!
BGP hijacks are very common nowadays
Tips
- Start with external entities outside of trust boundaries
- More controlled = Less dangerous
- Include (seemingly) uninterested threats
- More comprehensive = Less dangerous
- Focus on feasible threats
- Less practical = Less dangerous
Mitigations
To address an identified network threat, we first decide the desired action.
- Mitigation
- Make it harder to take advantage of a threat
- e.g., RPKI to mitigate BGP hijacks
- Elimination
- Remove exploited features
- e.g., no BGP messages = no hijack (naively)
- Also damage benign use cases
- Transferring
- Let someone else handle the risk
- e.g., let firewall filter excessive messages
- Risks are not transferable
- Accepting
- Ignore the impractical threats
- e.g., DoS by physically destroying routers
- Risks are underestimated
- Ignore the impractical threats
Mitigation is usually the best option.
Mitigation techniques against threats found by applying STRIDE
| Problem | Solution |
|---|---|
| Spoofing | Authentication (IPSec, DNSSEC, PKIs) |
| Tampering | Integrity |
| Repudiation | Logging |
| Information Disclosure | Confidentiality (encryption) |
| Denial of Service | Availability (filters, throttling) |
| Elevation of Privileges | Authorization (access control) |
Tips
- Validate that threats are addressed
- Perform a QA process to confirm
- Try to predict adversary’s moves against mitigations
- Involve economic advantages in arms races
- Update model in an iterative process
- New mitigation components may change the model
DDoS Attacks
DDoS attacks:
- use different sources (e.g., botnets) of traffic
- exhaust network resources (e.g., devices, links)
- affect many (if not all) networked systems
Common DDoS attack types
| Type | Unit | Description |
|---|---|---|
| Volumetric | bps | Sending massive traffic to create congestion e.g., DNS amplification |
| Protocol | pps | Exploiting weaknesses of the network protocols e.g., SYN flood |
| Application | rps | Exploiting weaknesses of targeted applications e.g., HTTP flood |
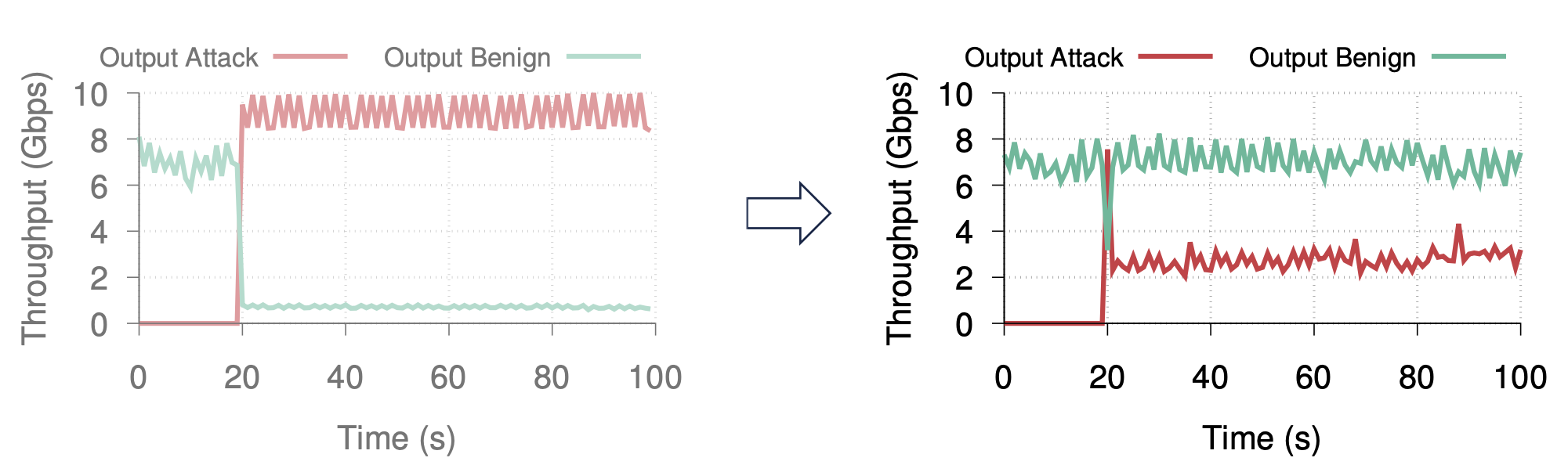
DDoS attacks always become more threatening In 2023, Google mitigated $398$ Mrps. 
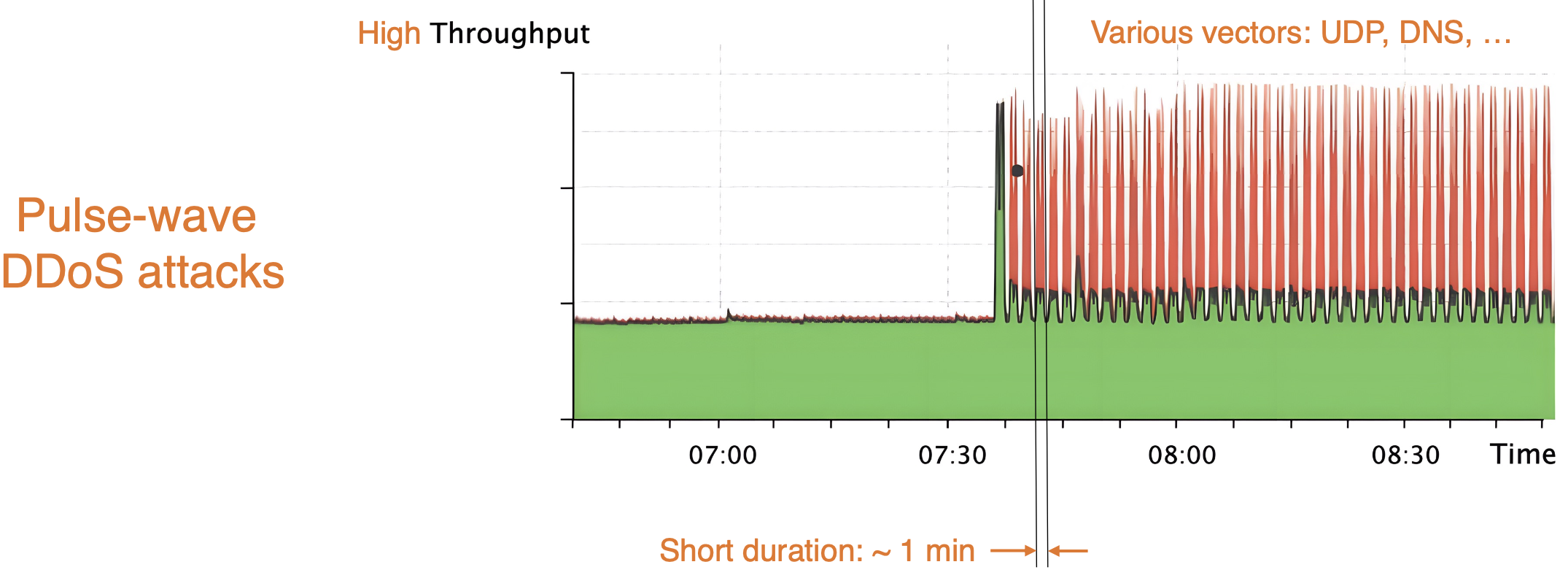
Pulse-wave DDoS attacks
Challenges:
- Short pulses: controller may not react in time
- Unknown attack vectors: unsupervision leads to misclassification
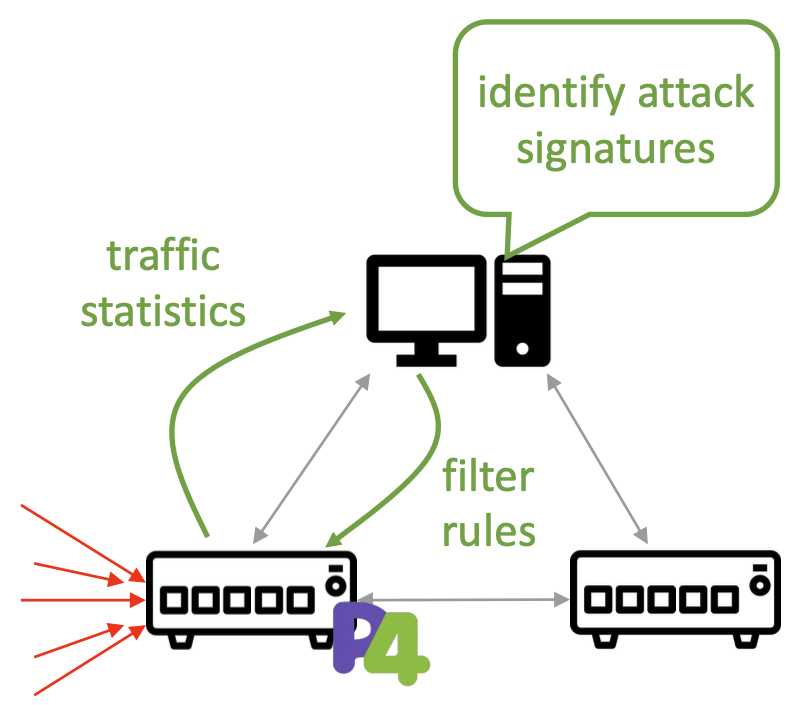
ACC-Turbo’s solutions:
- infer attacks in the data plane
- de-prioritize (not drop) clustered traffic
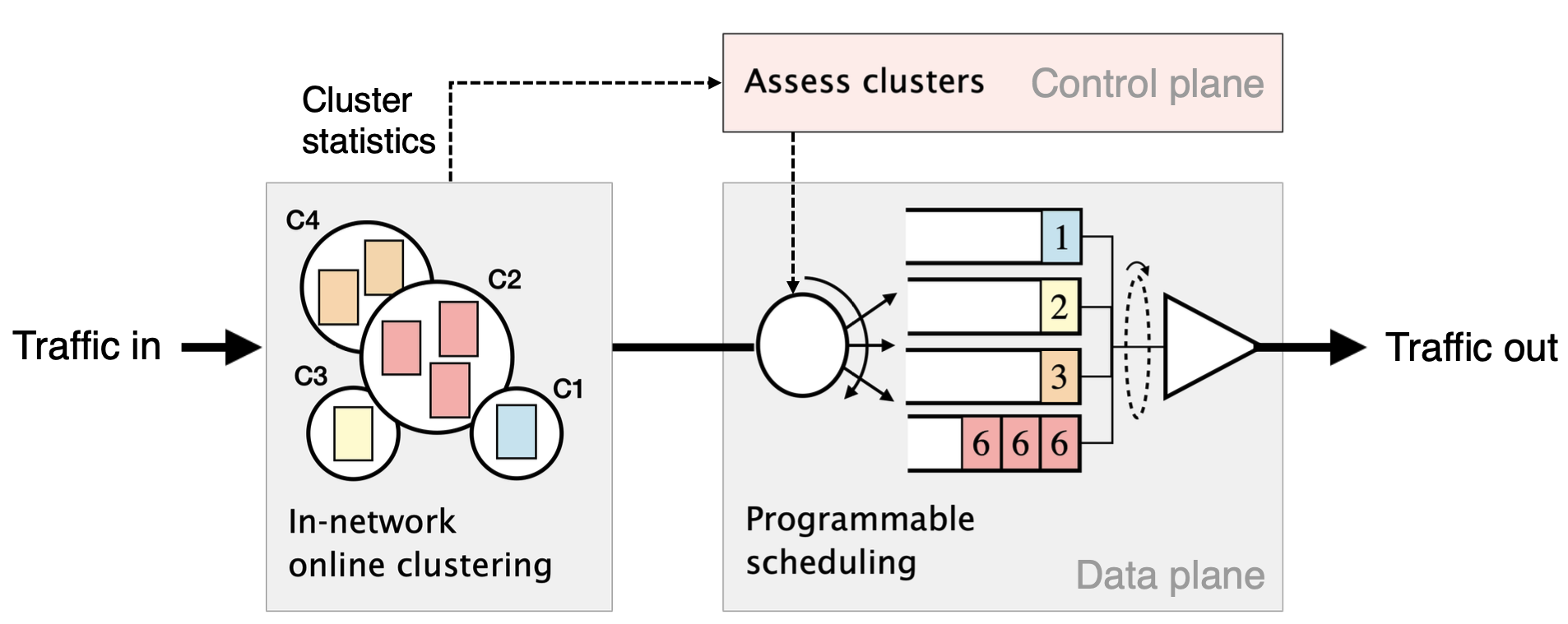
ACC-Turbo’s design
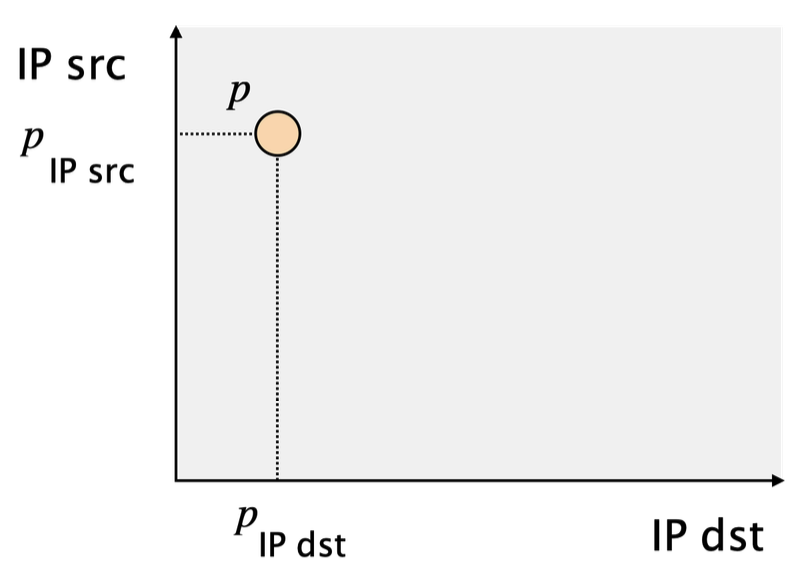
Clustering packets
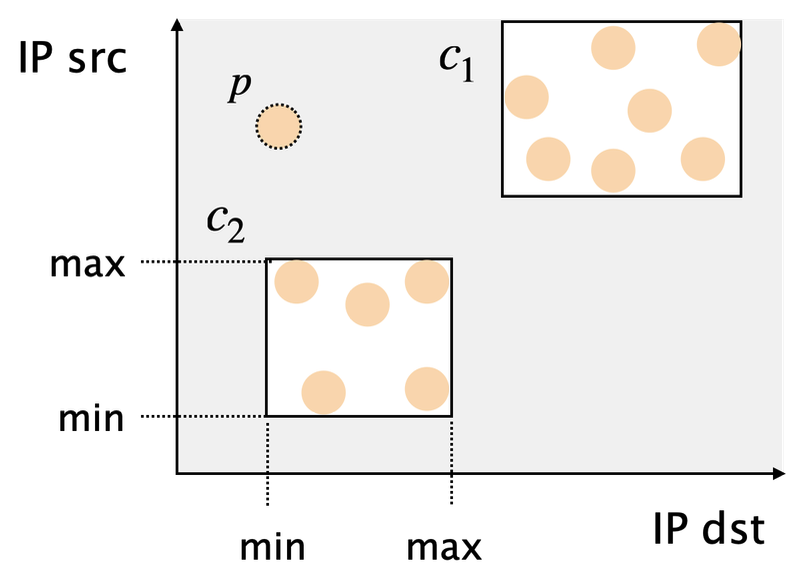
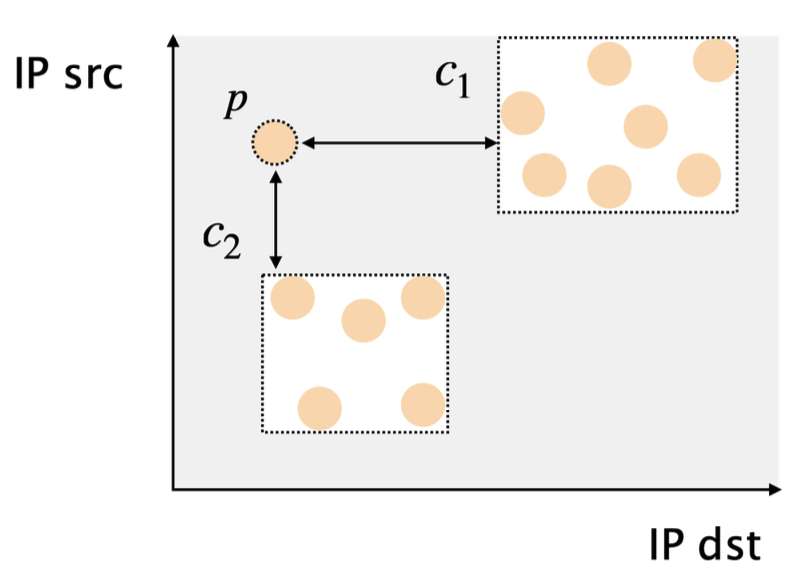
Map each arriving packet to the closest cluster
- Represent packets by points in the header space
- Represent clusters using registers/bloom filters
- Use Manhattan distance for easy implementation
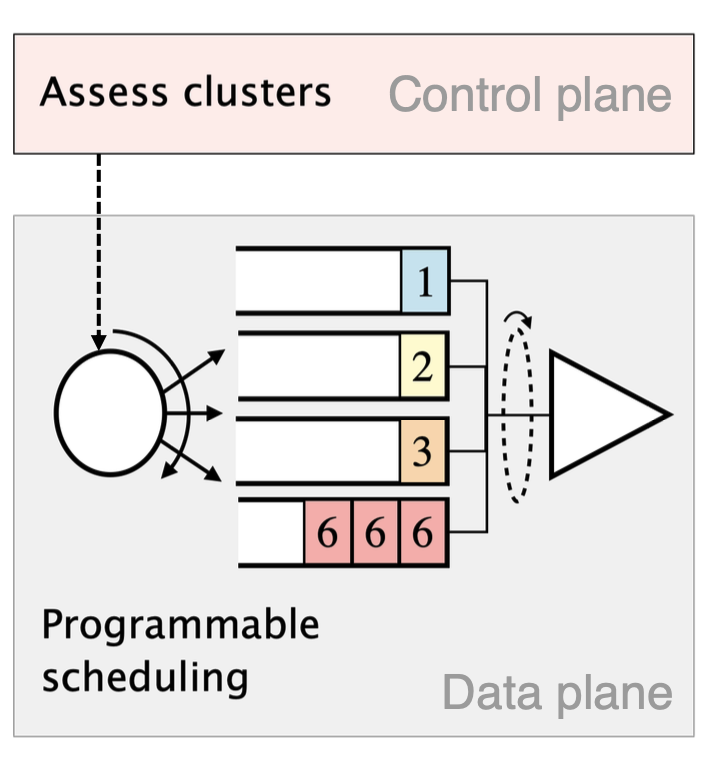
Controlling clustered packets
De-prioritizing malicious clusters via scheduling.
- Exact cluster statistics
- e.g., rate, size from data plane
- Assess clusters
- e.g., small clusters with higher rate are more malicious
- Synthesize scheduling policy
- Deprioritize most malicious clusters